Following up to the post on renaming windows 10 devices that are managed by Intune, another frequent requirement is remove the local user accounts from Administrators group. The AAD user account will be provisioned as Standard User and hence removing the local user accounts from Admin group is critical to secure the device from unauthorized privileged access. This can also be accomplished using PowerShell script given below.
$computerName = hostname
$LocalGroupName = "Administrators"
$Group = [ADSI]("WinNT://$computerName/$localGroupName,group")
$Group.Members() |
foreach {
$AdsPath = $_.GetType().InvokeMember('Adspath', 'GetProperty', $null, $_, $null)
$A = $AdsPath.split('/',[StringSplitOptions]::RemoveEmptyEntries)
$Names = $a[-1]
$Domain = $a[-2]
If ($Domain -eq $ComputerName -and $Names -ne "Administrator") {
Add-Content C:WindowsTempRemoveUsersFromAdminGroup.log "User $Names found on computer $computerName ... "
$Group.Remove("$AdsPath")
Add-Content C:WindowsTempRemoveUsersFromAdminGroup.log "Removed"
}
}Below are the high-level steps to be performed.
- Create AD Device Security Group with Static or Dynamic Membership rules (example: include all Azure AD Domain joined machines)
- Create a PowerShell Script with commands to remove users from Administrators group.
- Configure PowerShell Script profile in Intune and upload the created script.
- Assign the profile to AD Device Security group created in Step 1.
- Review the status based on user or device.
Please follow the steps from this post and replace the PS Script with above one to remove local users from Administrators group. Once you deploy the PowerShell Script Configuration Profile and wait for the sync to happen, the local accounts which are part of Administrator Group will get removed. You can find the logs in C:WindowsTempRemoveUsersFromAdminGroup.log
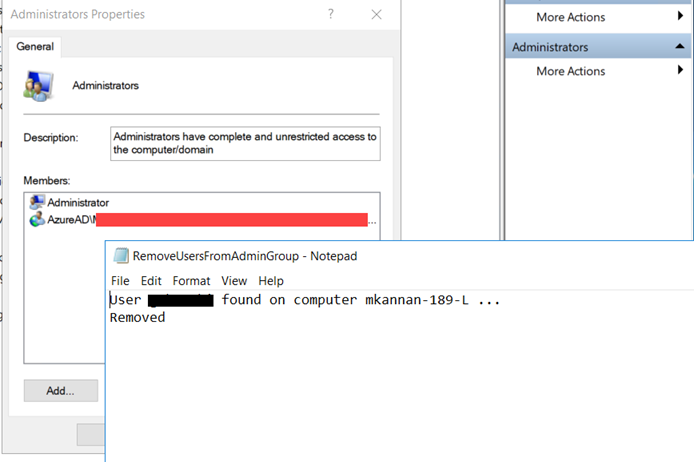
Hurray! The local user account(s) has/have been automatically removed from the Administrators group.

I followed all the steps correctly however the PowerShell script failed.
I created a Static Device based group, added the device manually where a user is logged in.
pushed the PowerShell script and it failed then what should be the root cause of it and further what can we do to fix it